In today’s digital landscape, proxy vs firewall is a common comparison when it comes to securing networks and managing online traffic. Both tools are widely used in cybersecurity, but they serve very different purposes.
According to recent reports, over 90% of organizations use firewalls to block unauthorized access and protect internal systems. Meanwhile, nearly 70% rely on proxy servers to control outbound requests and improve user privacy.
But what exactly separates a proxy from a firewall? Do you need both, or can one replace the other?
This guide breaks down how proxies and firewalls work, where they differ, and how using them together can enhance your digital security strategy.
What is a Proxy Server?
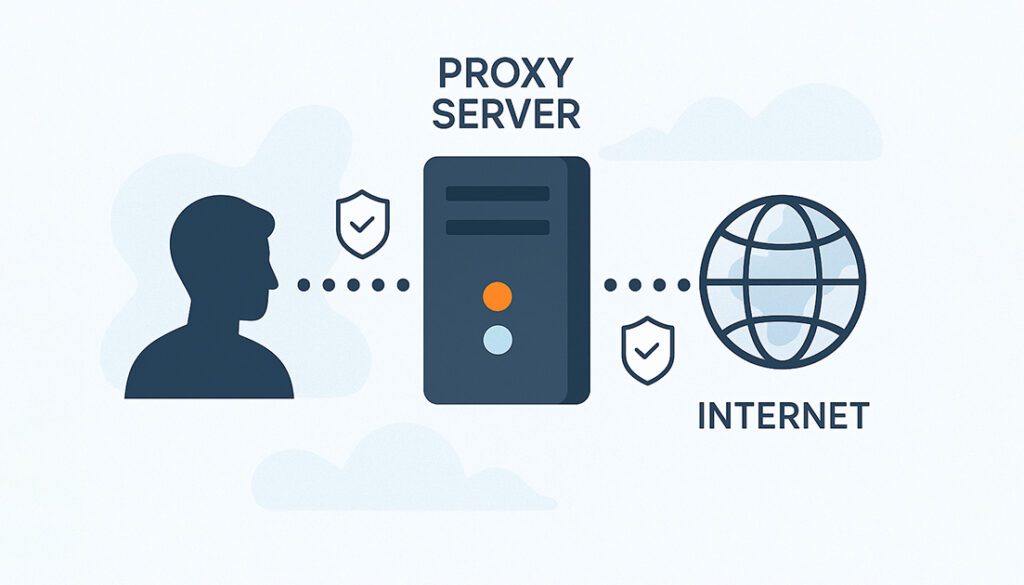
A proxy server is a gateway between your device and the internet. Instead of your computer directly connecting to a website, the request is rerouted through the proxy—allowing it to hide your real IP address, manage access, and add a layer of anonymity.
🔍 How Does It Work?
When you use a proxy:
- You send a request to access a website.
- The proxy forwards that request on your behalf.
- The response is returned through the proxy, then sent back to you.
This process helps mask your location, control access, and filter web traffic.
🕵️ Common Use Cases for Proxies
- ✅ Anonymous browsing and hiding your IP address
- ✅ Accessing geo-blocked or restricted websites
- ✅ Web scraping and data automation
- ✅ Content filtering in schools or corporate networks
🔄 Types of Proxy Servers
- Forward Proxy: The most common type; routes outbound traffic to the internet.
- Reverse Proxy: Used by servers to handle inbound traffic efficiently and securely.
- Transparent Proxy: Invisible to users, often used by organizations for monitoring or caching.
For more detailed approach, check out this article: What is a Proxy server.
📌 Important Note
Proxies operate at the application layer (Layer 7), meaning they only affect specific programs—not your entire system.
They do not provide encryption, which makes them less secure for sensitive tasks compared to firewalls or VPNs.
What is a Firewall
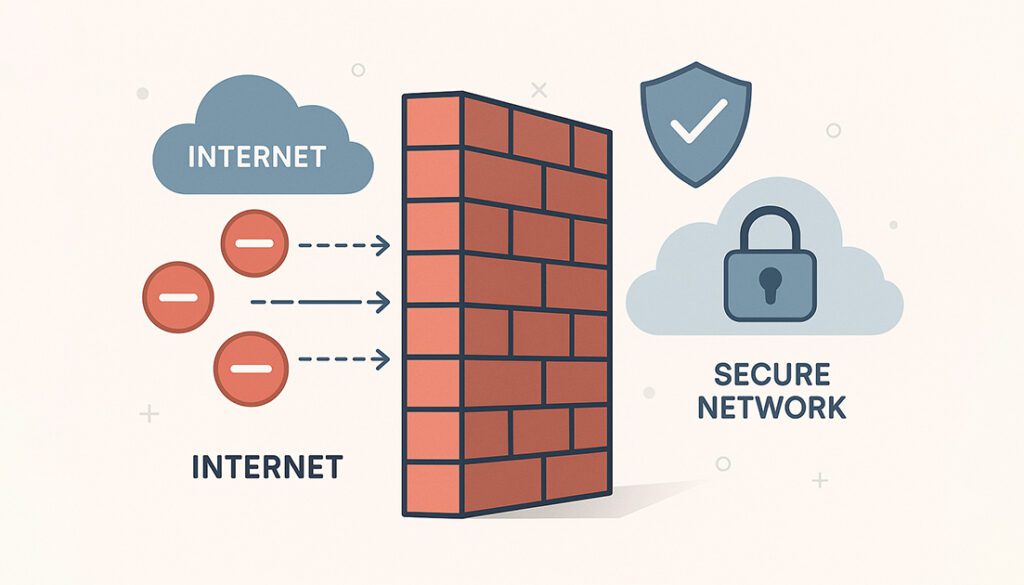
A firewall is a security system designed to monitor and control network traffic, acting as a digital gatekeeper between your internal network and the outside world. Its main job is to block unauthorized access while allowing legitimate communication to pass through.
🔍 How Does It Work?
Firewalls inspect incoming and outgoing traffic based on a set of predefined rules. They filter packets and decide whether to allow, block, or flag them based on source, destination, port, and protocol.
🛡️ Common Use Cases for Firewalls
- ✅ Blocking hackers and malicious traffic
- ✅ Preventing unauthorized access to internal systems
- ✅ Segmenting network traffic for better control
- ✅ Enforcing security policies in business environments
🧱 Types of Firewalls
- Packet-Filtering Firewall: Examines data packets and filters based on rules.
- Stateful Firewall: Tracks active connections and makes dynamic decisions.
- Proxy Firewall: Acts as an intermediary between users and services (like a proxy server with filtering).
- Next-Gen Firewall (NGFW): Adds features like intrusion prevention, deep packet inspection, and app control.
📌 Important Note
Firewalls typically operate at lower OSI layers (3 and 4)—the network and transport layers—making them ideal for system-wide protection and traffic filtering.
They’re a foundational layer in any serious cybersecurity strategy.
Proxy vs Firewall: Key Differences

While both proxies and firewalls are essential to network security, they serve different purposes, operate at different layers, and offer distinct protections. Here’s how they compare across key areas:
🧠 Functionality
- Proxy Server: Acts as an intermediary between users and external services. It routes and filters outgoing traffic.
- Firewall: Acts as a gatekeeper for all network traffic—both inbound and outbound. It enforces security policies based on traffic rules.
🧬 Layer of Operation
- Proxy: Operates at the application layer (Layer 7)—managing specific programs like web browsers.
- Firewall: Typically functions at the network and transport layers (Layers 3 & 4)—monitoring all traffic between networks or devices.
🔒 Security Capabilities
- Proxy: Provides basic privacy and control but usually lacks encryption or deep packet inspection.
- Firewall: Offers advanced protection features such as intrusion prevention, traffic filtering, and packet inspection.
🛠️ Configuration and Use
- Proxy: Often configured per application. Lightweight and ideal for users needing anonymity or IP masking.
- Firewall: Configured at the network level. Essential for businesses or individuals who want to block threats system-wide.
⚙️ Performance and Overhead
Firewall: Can add latency if deep inspection or filtering is heavily used—though modern firewalls minimize this.
Proxy: Minimal resource usage unless handling massive traffic volumes.
🔄 Proxy Server
- Role: Intermediary for outgoing traffic
- Layer: Application Layer (Layer 7)
- Traffic: Outbound only
- Security: IP masking, no encryption
- Use Cases: Anonymity, scraping, bypassing blocks
🧱 Firewall
- Role: Security barrier for inbound & outbound traffic
- Layer: Network & Transport Layers (3 & 4)
- Traffic: Both directions
- Security: Deep filtering, threat prevention
- Use Cases: System-wide protection, policy enforcement
When to Use a Proxy, a Firewall, or Both
While proxies and firewalls each play a unique role, they’re not always used in isolation. Understanding when to use one or both, can help you strike the right balance between security, performance, and control.
🔄 When to Use a Proxy
- Hide your IP address for anonymity
- Bypass geo-blocks and filters
- Perform web scraping or automation
- Filter content on specific applications
🧱 When to Use a Firewall
- Block malicious traffic and intrusions
- Protect your home or business network
- Enforce IP, port, or protocol-level policies
- Prevent malware, DDoS, and unauthorized access
🔄+🧱 When to Use Both
- Combine threat protection with anonymity
- Use proxy for outbound privacy, firewall for inbound filtering
- Improve security in business or enterprise networks
- Create a multi-layered defense architecture
Using both together creates a multi-layered security architecture that combines anonymity, access control, and active threat prevention, ideal for modern network security needs.
Cost Considerations and Value Proposition
While both proxies and firewalls contribute to network protection, their costs and value vary based on usage, deployment, and features.
Proxy servers
Proxy servers are generally affordable, especially for individual users or specific use cases like web scraping, bypassing geo-blocks, or managing automation tools. Pricing typically ranges from $0.15 to $3 per month, depending on whether you’re using datacenter, residential, or mobile IPs. Some proxy services charge by bandwidth or per IP address, offering flexibility for different needs.
Popular providers include:
Firewalls
Firewalls, on the other hand, come in both free and paid options. Most operating systems include a basic firewall, which works well for individual users. However, enterprise-level firewalls—which offer advanced filtering, monitoring, and threat detection can range from $100 to $500+, depending on the features and deployment scale.
Common enterprise vendors include:
In summary, proxies are cost-effective tools for privacy and content access, while firewalls offer deeper, more comprehensive protection at a higher (but worthwhile) cost for business or network-wide security.
🔄 Proxy Cost & Value
- Prices range from $0.15 to $3 per month
- Flexible options: pay-per-IP or bandwidth
- Great for scraping, automation, and bypassing restrictions
🧱 Firewall Cost & Value
- Built-in software firewalls are free on most OS
- Enterprise-grade firewalls cost $100–$500+
- Ideal for protecting entire networks and enforcing policies
Pros and Cons: Proxy vs Firewall
Before deciding which tool is right for your setup, it’s important to weigh the strengths and limitations of both proxies and firewalls. Here’s a quick breakdown to help you compare their core advantages and drawbacks.
🔄 Proxy Server
✅ Pros:
- Hides IP address for anonymity
- Bypasses geo-blocks and restrictions
- Useful for scraping and automation
- Lightweight and easy to configure
❌ Cons:
- No encryption or deep security
- Works only at the application level
- Can be blocked by advanced firewalls
🧱 Firewall
✅ Pros:
- Blocks threats and unauthorized access
- Monitors inbound and outbound traffic
- Supports policy enforcement and segmentation
- Provides deeper, system-wide protection
❌ Cons:
- Can be complex to configure
- Higher cost for enterprise features
- May require technical knowledge
FAQs: Proxy vs Firewall
What is the main difference between a proxy and a firewall?
A proxy server filters outgoing traffic and hides user identities, while a firewall filters both incoming and outgoing traffic to block unauthorized access. Firewalls offer more comprehensive system-level protection.
Can I use both a proxy and a firewall together?
Yes. In fact, using both is recommended for enhanced security. A proxy offers privacy and content control, while a firewall provides strong inbound threat protection.
Does a proxy replace a firewall?
No. A proxy helps manage outbound access and anonymity but doesn’t offer the deep security features of a firewall. You still need a firewall to block threats and unauthorized access.
Are proxies secure?
Proxies provide basic privacy by hiding your IP address, but they usually lack encryption. For secure data transmission, you’ll need a VPN or an encrypted firewall.
Are firewalls only for businesses?
Not at all. Most operating systems (like Windows and macOS) come with built-in firewalls. However, businesses often use more advanced firewall appliances or software for additional layers of protection.
Do firewalls and proxies slow down internet speed?
They can, but usually not significantly.
- Proxies may introduce slight delays depending on routing and server load.
- Firewalls can slow down traffic if performing deep packet inspection, but modern systems are optimized to minimize this.
Which is easier to set up: a proxy or a firewall?
Proxies are generally easier to configure for individual applications or browsers.
Firewalls, especially enterprise-grade ones, can be more complex and often require IT knowledge for proper rule creation and network segmentation.
Conclusion: Which One Do You Need?
Both proxies and firewalls serve essential but distinct roles in network security.
Use a proxy server if your priority is anonymity, content access, or task-specific control like scraping or bypassing geo-blocks.
Rely on a firewall when you need full network protection, traffic monitoring, and defense against malicious threats.
For the best results, many individuals and organizations use both together a proxy for privacy and flexibility, and a firewall for strong system-wide security.
Understanding how each tool works helps you build a smarter, layered defense strategy for your digital environment.


