Wondering if a proxy can see what you’re doing on an HTTPS connection? You’re not alone. With more people using proxies to access content or hide IPs, it’s important to understand how safe your data really is. The big question is: can a proxy read HTTPS traffic, or does encryption keep you secure?
In this guide, we’ll explain how HTTPS works, what proxies can and can’t access, when interception might happen, and how to protect yourself, especially on public or corporate networks.
For a deeper look at how VPNs compare, check our Proxy vs VPN comparison.
How HTTPS Works (In Simple Terms)
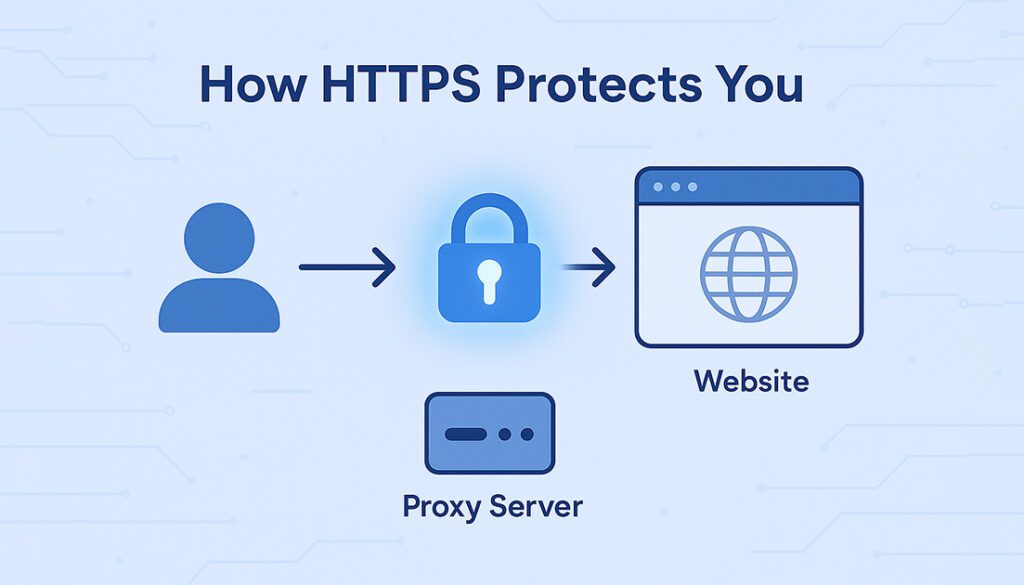
HTTPS (Hypertext Transfer Protocol Secure) protects your connection by encrypting all data exchanged between your browser and a website. That means even if someone like a proxy or Wi-Fi provider tries to peek in, they won’t see anything useful.
🔐 What HTTPS Does:
🧬 Encryption
HTTPS scrambles your data, making it unreadable to proxies and snoopers.
🔑 Authentication
Ensures you’re connected to the real website, not a fake or proxy in disguise.
🔒 Data Privacy
With HTTPS, a proxy can only see the domain name, not what you do on the site.
Without HTTPS, proxies can easily view everything you type or click. With HTTPS, they only see the domain, not the page content, data, or actions.
What Proxies Can and Can’t See Over HTTPS
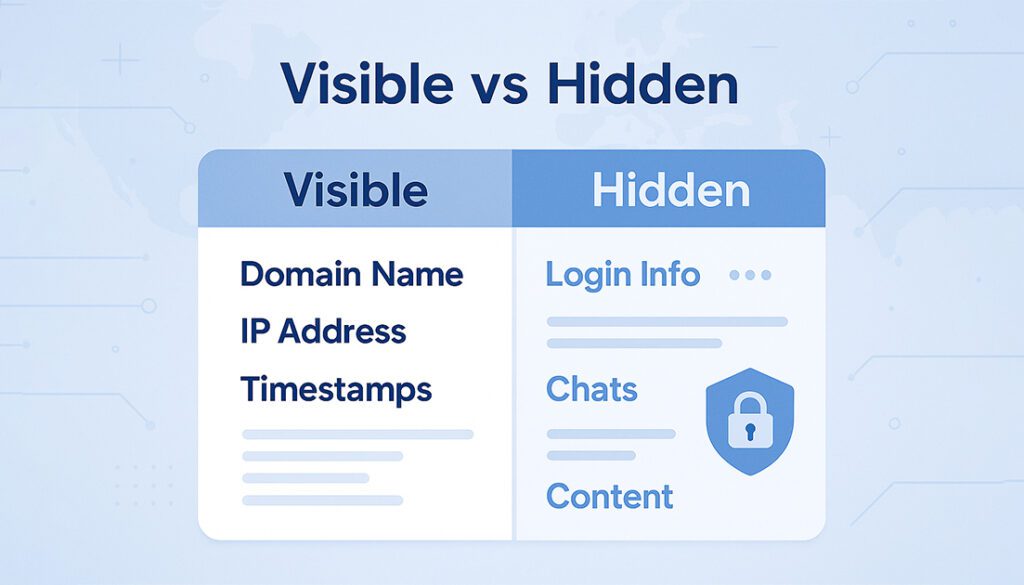
A proxy server acts as a middleman, but that doesn’t mean it has full visibility. When HTTPS is involved, the data is encrypted from end to end, which limits what the proxy can observe.
👀 What Proxies Can See
- Website domain (e.g., example.com)
- Data size sent or received
- Destination IP address
- Connection timestamps
🙈 What Proxies Can’t See
- Pages visited (e.g., /login, /checkout)
- Login credentials or form data
- Messages, chats, or streaming content
- Cookies or tracking session info
Unless a proxy is designed to intercept HTTPS (see next section), it can’t read the actual content, just metadata.
Can Proxies Decrypt HTTPS Traffic?
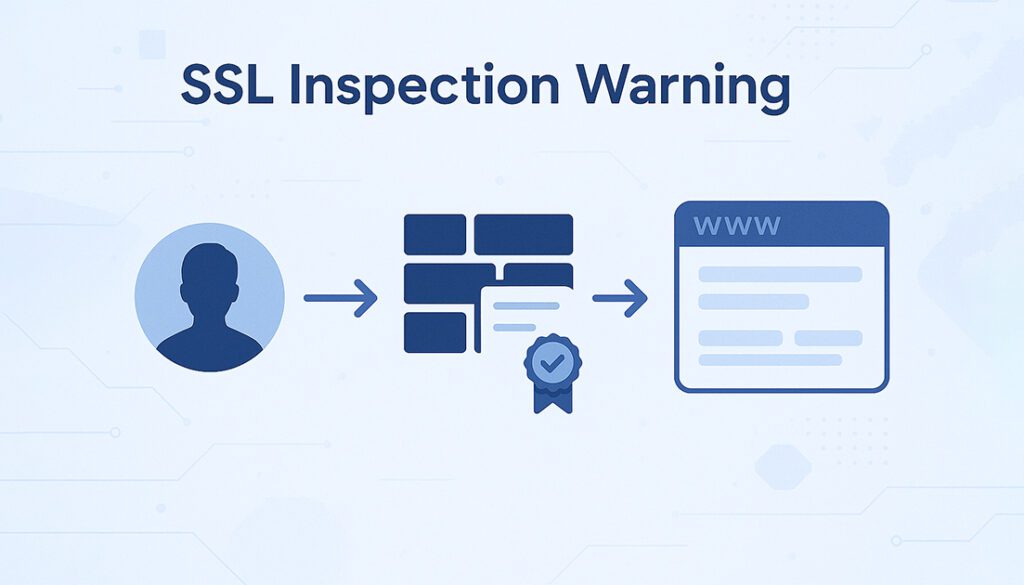
By default, no, proxies cannot decrypt HTTPS because the connection is encrypted end-to-end between your browser and the website. But there are exceptions where proxies are specifically configured to intercept and decrypt that traffic.
🛡️ Where Proxies Decrypt HTTPS
- Corporate networks with SSL inspection enabled
- Parental control systems or filtering apps
- School or university-managed devices
- Enterprise-grade firewalls (e.g., Fortinet, Palo Alto)
🔍 How MITM Decryption Works
- Proxy installs a custom root certificate on your device
- Your browser “trusts” the proxy as the destination
- Proxy decrypts and inspects HTTPS traffic
- It then re-encrypts the data before sending it to the site
⚠️ If you didn’t knowingly install a certificate, the proxy cannot break HTTPS.
Safe vs Risky Proxy Use Cases

Not all proxies are dangerous, but knowing when to trust them makes all the difference. Here’s how to tell the difference between a privacy-respecting setup and one that could be reading your traffic:
✅ Safe Proxy Use Cases
- Anonymous browsing with HTTPS
- Bypassing region locks or censorship
- Trusted browser extensions
- Paid proxies with clear privacy policies
⚠️ Risky Proxy Use Cases
- Free proxies with no transparency
- SSL-inspecting corporate firewalls
- Public Wi-Fi proxies without consent
- Any proxy requiring certificate installation
🕵️ When in doubt, stick to HTTPS and use a trustworthy VPN or proxy provider.
Tips to Protect Your HTTPS Traffic
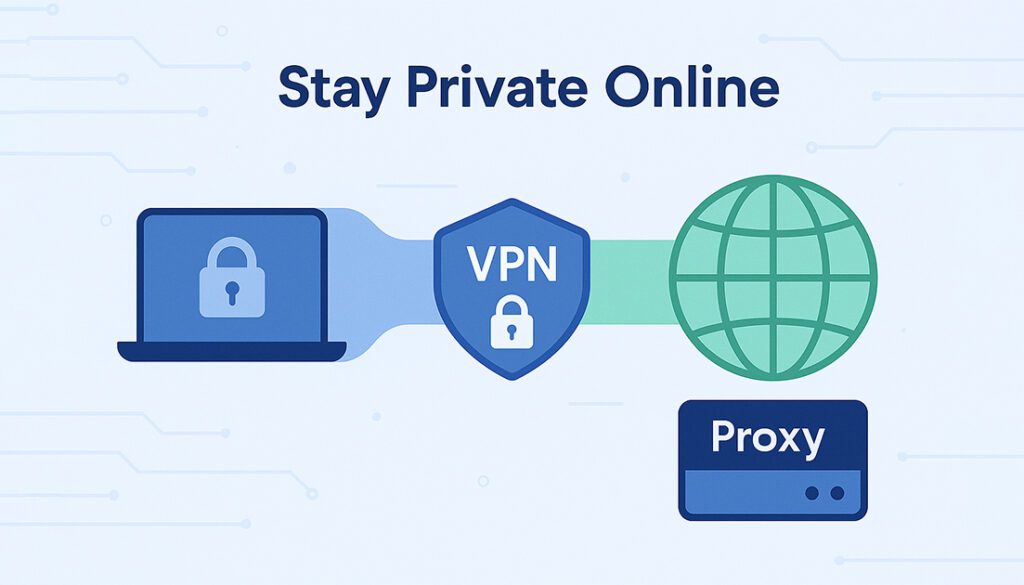
If you want to keep your encrypted traffic truly private even from proxies, follow these best practices:
🛡️ Practical Security Tips:
🚫 Avoid Free Proxies
Untrusted proxies may log or redirect your encrypted traffic without consent.
🔐 Use a VPN
A reliable VPN encrypts everything before your ISP or proxy sees it.
⚠️ Don’t Install Unknown Certificates
Avoid giving proxies access to decrypt your HTTPS unless you fully trust them.
🔒 Check for the Padlock
Always use secure HTTPS websites, look for the 🔒 icon in your browser.
🧠 Use DNS over HTTPS (DoH)
Prevents DNS leaks and hides which sites you’re visiting from your ISP or proxy.
🔍 Test for Interception
Sites like BadSSL.com help detect if HTTPS traffic is being inspected or intercepted.
Encryption protects you, but only if you know how to keep it that way.
Not all proxies are safe or legal — learn more in Are Proxies Illegal?
FAQs
Can a proxy read HTTPS traffic?
No. Standard proxies cannot read or decrypt HTTPS traffic. The data is encrypted end-to-end between your device and the destination server.
Is HTTPS traffic completely secure from proxies?
Mostly, yes, unless you install a custom certificate (like on corporate networks), the proxy cannot decrypt the content of HTTPS.
Can HTTPS be intercepted by companies or schools?
Yes, if they use SSL inspection and install a trusted certificate on your device. This allows the proxy to act as a man-in-the-middle.
Do free proxies decrypt HTTPS?
Most free proxies don’t have the ability to decrypt HTTPS, but some may still collect metadata or redirect traffic. Avoid them for sensitive use.
Can a proxy see which pages I visit on HTTPS sites?
No. It can only see the domain (e.g., example.com), not the specific pages or content inside the site.
What kind of proxy can decrypt HTTPS?
Only advanced proxies with SSL inspection often used in businesses, schools, or security tools, can decrypt HTTPS with the right setup.
How do I know if a proxy is reading my HTTPS traffic?
Look for certificate warnings or inspect installed certificates. You can also use test sites like BadSSL.com to check for MITM interception.
How can I keep my HTTPS traffic private?
Use a trusted VPN, avoid installing unverified certificates, and stick to secure websites with a padlock icon.
Final Thoughts
So, can a proxy read HTTPS? In most cases, No. If you’re using a secure connection, your private data stays hidden from any basic proxy server. But there are exceptions. If you’re on a corporate, school, or public network that uses SSL inspection, someone may be able to peek inside, especially if you’ve installed a certificate without realizing it.
The key is awareness. Stick with HTTPS, don’t trust unknown proxies, and use a VPN for added protection. When privacy matters, every layer counts.
Need more control over what proxies can and can’t do? Check out our guide to the best proxy type.
Worried About Proxy Interception?
A trusted VPN encrypts your traffic from end to end — making it unreadable to proxies, ISPs, or bad actors. Stay secure on any network.
View Top VPNs

