Can proxy bypass firewall restrictions in schools, workplaces, or public networks? It’s a common question for anyone dealing with blocked websites or limited online access. Firewalls act as gatekeepers, deciding which data can enter or leave your network and they’re often used to prevent you from reaching certain apps, platforms, or services.
But what if you need access to something important? That’s where proxies come in.
A proxy can sometimes help you bypass a firewall by routing your traffic through a different server. Whether it works or not depends on the type of firewall, the proxy setup, and how both are configured. In this guide, we’ll explain how firewalls function, how proxies interact with them, and when a proxy might be the right solution to get past those digital walls.
Understanding Firewalls
Firewalls are essential tools that protect networks from unauthorized access, malware, and data leaks. They filter internet traffic based on rules and can block or allow data depending on where it comes from, what it contains, or where it’s going.
Whether you’re at school, work, or using public Wi-Fi, there’s usually a firewall in place. But not all firewalls work the same way, some are basic, while others are highly advanced.
🔍 Common Types of Firewalls
🔸 Packet-Filtering Firewall
Examines traffic based on basic criteria like IP address, port, and protocol. It’s simple but effective for basic filtering.
🔸 Stateful Inspection Firewall
Tracks active connections and evaluates traffic based on the state of the connection, offering more dynamic security.
🔸 Application-Layer Firewall
Operates at the application level to inspect and block specific content or user actions, like certain URLs or file types.
🔸 Next-Generation Firewall (NGFW)
Integrates deep packet inspection, intrusion prevention, and application awareness. It’s one of the hardest to bypass.
🧱 Common Uses of Firewalls in Network Security
Firewalls are used for many important tasks in network security:
- ✅ They block bad web traffic to stop data breaches.
- ✅ They enforce security rules by controlling access to certain resources.
- ✅ They manage access to sensitive data to protect against threats.
- ✅ They help with web filtering to block dangerous websites.
Understanding firewalls and their roles helps us see how proxies can bypass them. This knowledge is crucial for improving security practices.
What Is a Proxy Server?
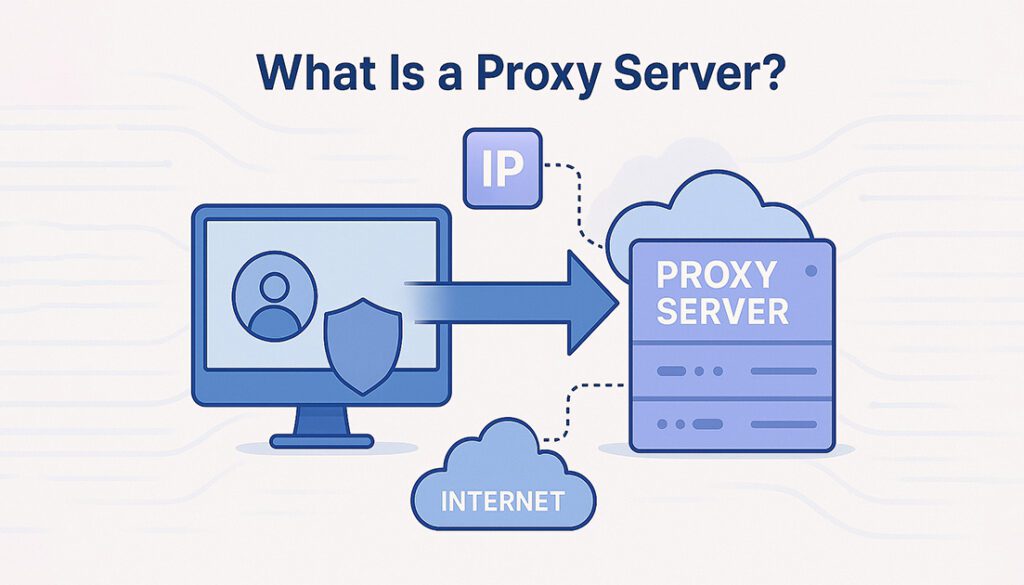
A proxy server sits between your device and the internet. Instead of connecting directly to a website, your traffic is routed through the proxy first. This setup can hide your IP address, enforce content filters, or log network activity.
There are two main ways to categorize proxy servers: by behavior and by protocol. Here’s a breakdown:
🔄 Behavioral Proxy Types
🔹 Forward Proxy
Routes client requests to external resources. Most common for users trying to bypass restrictions or stay anonymous.
🔹 Reverse Proxy
Sits in front of a server to handle incoming requests. Often used for load balancing, caching, and DDoS protection.
🔹 Transparent Proxy
Intercepts traffic without modifying requests or hiding IPs. Common in schools and offices for monitoring purposes.
🔹 Anonymous Proxy
Hides your real IP from websites but may identify itself as a proxy. Useful for privacy and content access.
⚙️ Technical Proxy Protocols
🔸 HTTP Proxy
Handles web traffic only. Often used for basic browsing or website access filtering. Doesn’t support encryption.
🔸 HTTPS Proxy
Secures traffic with SSL/TLS. Better for safe anonymous browsing and accessing secure websites.
🔸 SOCKS Proxy
Works at a lower level than HTTP. Supports all traffic types—great for P2P, gaming, and bypassing firewalls.
For more on proxy servers, check out this article.
How Proxies Interact with Firewalls
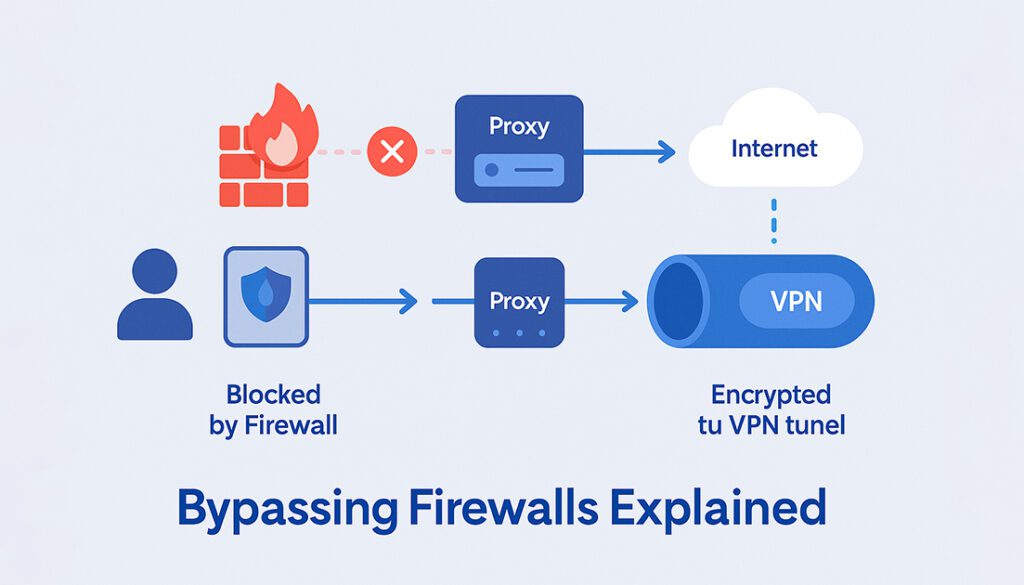
To understand if and how a proxy can bypass a firewall, it’s important to see how both technologies operate on the network level.
A firewall filters traffic by analyzing packet headers, port numbers, protocols, and even application data. If traffic matches a blocked rule, it’s denied. In contrast, a proxy forwards your request through a different IP, masking the original source and potentially helping it slip past firewall restrictions.
✅ When Proxies Can Bypass Firewalls
- Unrestricted Ports: If the firewall allows common ports like 80 (HTTP) or 443 (HTTPS), a proxy using those ports might pass through unnoticed.
- No Deep Packet Inspection (DPI): Without DPI, firewalls often can’t detect or block proxy traffic effectively.
- Use of SOCKS5 Proxies: SOCKS proxies are more versatile and can handle various traffic types, making them harder to detect.
- Lack of IP Blocklists: If the firewall isn’t using an updated IP blocklist, it might not recognize the proxy server as a threat.
❌ When Proxies Can’t Bypass Firewalls
- Strict DPI Filtering: Firewalls using DPI can detect and block proxy traffic by analyzing packet behavior or header mismatches.
- Blocked Proxy IPs: Many firewalls subscribe to databases that list known proxy IP addresses and block them outright.
- Port Restrictions: If only specific ports are allowed, proxy connections using non-standard ports will be dropped.
- Transparent Proxies Exposed: Some proxies don’t hide your IP or modify requests. These are easily detected and blocked.
🧠 Summary Insight
Proxy vs VPN for Bypassing Firewalls
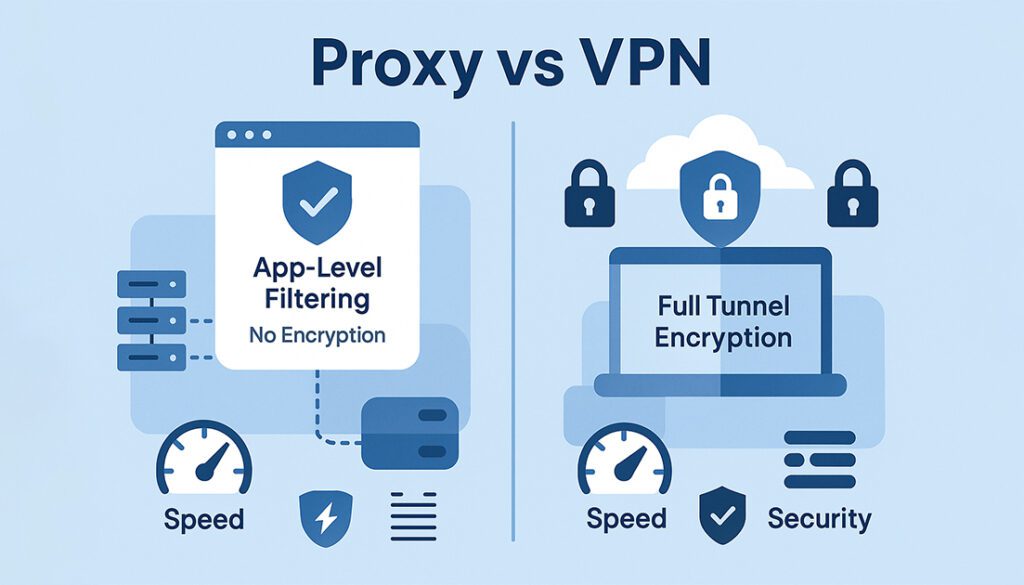
While proxies can sometimes get around firewalls, they aren’t always the most reliable method. VPNs offer stronger encryption, stealth features, and consistent success with bypassing even advanced filtering systems.
Let’s compare how proxies and VPNs handle firewalls:
🔍 Comparison Table
| Feature | Proxy | VPN |
|---|---|---|
| Encryption | ❌ None or minimal | ✅ Strong (AES 256-bit or more) |
| Bypass Success | 🔸 Limited to basic firewalls | ✅ High, even with DPI |
| Stealth Options | ❌ Lacks obfuscation | ✅ Obfuscation and stealth modes |
| Speed | ✅ Generally faster | 🔸 Slightly slower due to encryption |
| Privacy & Security | ❌ Weaker | ✅ Stronger protection |
When to Use a Proxy to Bypass a Firewall
While proxies aren’t as secure as VPNs, they still have practical use cases, especially when speed, simplicity, or access to specific content is your main goal.
Here are common situations where using a proxy makes sense:
🎓 School or Library Access
Use a proxy to access restricted websites like YouTube or Reddit when firewalls block them during browsing sessions.
🌐 Geo-Restricted Content
Bypass basic regional restrictions on websites that don’t have strong anti-proxy filters or DPI firewalls.
⚠️ Censored News Access
Access blocked news or information sites in regions where basic filtering is enforced but DPI is not deployed.
🕵️ Low-Risk Anonymity Tasks
Use for low-sensitivity anonymous browsing or simple scraping tasks that don’t require encrypted traffic.
Limitations and Risks of Using Proxies

IProxies can be helpful in certain scenarios, but they come with trade-offs, especially when it comes to privacy, reliability, and security. Here are the key downsides to consider:
🔓 No Encryption
Most proxies don’t encrypt your traffic, leaving your data exposed to snooping by ISPs, firewalls, or attackers.
🚫 Easy to Detect
Many proxies are blocked by modern firewalls that use IP blocklists, DPI, or protocol fingerprinting techniques.
📉 Unstable Performance
Free or overloaded proxy servers often result in slow speeds, dropped connections, or high latency.
🔐 No Built-in Security
Unlike VPNs, proxies don’t offer kill switches, DNS leak protection, or encrypted tunnels—putting sensitive data at risk.
Alternatives to Proxies for Firewall Bypass
If a proxy isn’t enough to beat your firewall, there are stronger and more secure alternatives available. These tools offer better encryption, stealth, and reliability when accessing restricted content or bypassing censorship.
🔐 VPNs (Virtual Private Networks)
VPNs encrypt all internet traffic and can bypass deep packet inspection, making them ideal for secure access across firewalls.
🌍 Tor Network
Routes traffic through multiple encrypted nodes. While slower than VPNs, Tor can evade advanced censorship and surveillance.
🛰️ Shadowsocks
A lightweight open-source proxy project often used in high-censorship countries. Harder to detect and block than standard proxies.
📶 Mobile Data Tethering
Using your phone’s data connection instead of Wi-Fi can help bypass local network firewalls temporarily.
Frequently Asked Questions
Can all proxies bypass firewalls?
No, not all proxies can bypass firewalls. It depends on the proxy type and the level of filtering the firewall uses. Transparent proxies are usually blocked easily, while SOCKS5 or stealth proxies have better chances.
What type of proxy is best for bypassing firewalls?
SOCKS5 proxies are generally the most effective, especially when combined with HTTPS or obfuscation features. They can handle various types of traffic and are harder for firewalls to detect.
Why does my proxy get blocked by the firewall?
Your proxy may be using a known IP address, port, or protocol pattern flagged by the firewall. Deep packet inspection (DPI) or proxy detection lists can also block proxy activity.
Can a reverse proxy bypass a firewall?
No. Reverse proxies are typically used for internal server-side control and security, not for client-side access or bypassing restrictions.
How do schools and workplaces block proxies?
They use a combination of DNS filtering, IP blacklists, port restrictions, and DPI to detect and block proxy traffic.
Are proxies legal to use for bypassing firewalls?
In most countries, using a proxy is legal. However, using it to access restricted content at work, school, or in censored regions may violate terms of use or local laws.
What’s safer for bypassing firewalls: VPN or proxy?
A VPN is safer. It encrypts all traffic, offers better stealth features, and is more reliable against modern firewall technologies.
✅ Final Thoughts: Can Proxy Bypass Firewall?
Proxies can bypass basic firewalls, especially those that don’t use deep packet inspection or aggressive IP blocking. They’re lightweight, easy to use, and useful for accessing restricted content in schools, libraries, or light censorship environments.
However, they lack encryption, stability, and stealth. If you’re facing stricter firewalls or value security and privacy a VPN is a more powerful and reliable option.
Knowing the difference between proxies and is key. It helps protect my online privacy and security.
Looking for a Reliable Proxy?
Need to bypass a firewall or access restricted content? Check out our top-rated proxy providers for speed, anonymity, and geo-access flexibility.
🔍 View Best Proxy Providers

