VPNs are often marketed as the ultimate privacy tool, a digital invisibility cloak. But a growing number of users are asking: Can a VPN actually be hacked?
The truth is, while VPNs do provide strong layers of encryption and anonymity, they’re not invincible. Poor setups, shady providers, or unpatched vulnerabilities can still put your data at risk.
In this article, we’ll break down what it really means for a VPN to be hacked, explore real-world breach examples, expose common VPN flaws, and share practical steps you can take to protect yourself.
If you’ve ever wondered how safe your VPN really is, or if you’re using the right one, you’re in the right place.
How Do VPNs Work & What Do They Actually Protect?
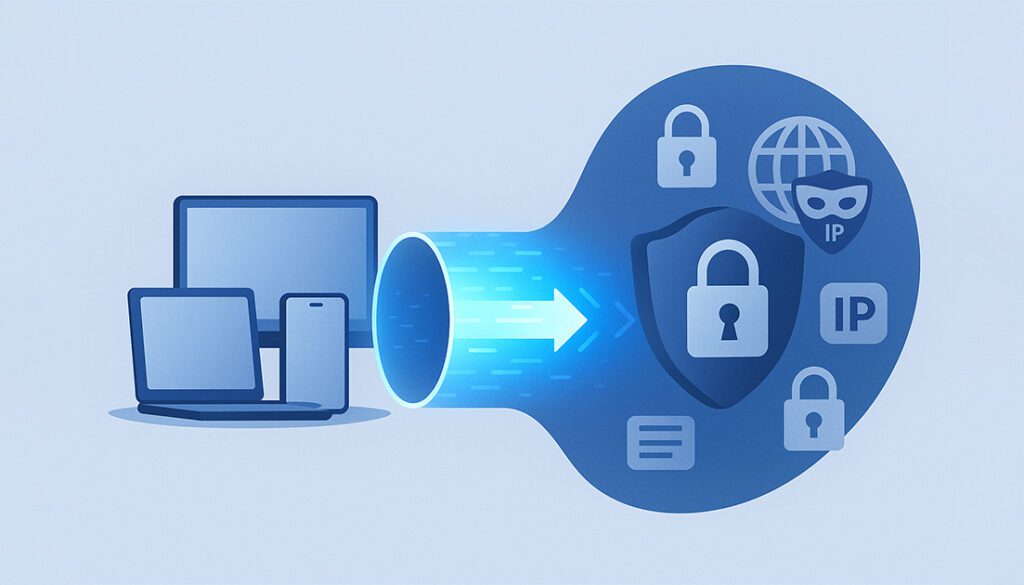
A Virtual Private Network (VPN) acts like a secure tunnel between your device and the internet. It encrypts your online traffic and routes it through a remote server, hiding your real IP address and replacing it with one from the VPN provider.
This means your activity is masked from websites, advertisers, internet service providers (ISPs), and even hackers. It’s especially useful when using public Wi-Fi, where your data would otherwise be wide open to surveillance or interception.
The main protections a VPN offers include:
- 🔒 Encryption: Scrambles your data so outsiders can’t read it
- 🛡️ Anonymity: Hides your IP and location
- 🌐 Bypass Restrictions: Lets you access geo-blocked or censored content
However, VPNs are not magic shields. They don’t stop malware, prevent phishing scams, or make you completely invisible online. Also, if a VPN service has poor security, leaks your IP or DNS data, or stores logs, your privacy can still be compromised.
– ISP tracking
– IP exposure
– Data interception on public Wi-Fi
– Geo-restricted content blocks
❌ A VPN Does Not Protect You From:
– Malware or viruses
– Clicking phishing links
– Bad VPN providers logging your data
– Unsafe browser extensions
Can VPNs Be Hacked? (Straight Answer)

The short answer: Yes, a VPN can be hacked, but it’s rare and not easy. Most quality VPNs use military-grade encryption and strong protocols that are practically unbreakable with today’s technology.
But hacking doesn’t always mean “breaking the encryption.” In the real world, most VPN-related hacks happen because of:
- 🔧 Misconfigurations (like DNS or IP leaks)
- 🧑💻 User mistakes (e.g., connecting without a kill switch)
- 🕵️ Shady VPN providers (selling or leaking your data)
- 💻 Exploits targeting the VPN software
It’s also important to understand that a VPN can be hacked indirectly. For example, if your device is infected with spyware or malware, the attacker can see what you do online, even if you’re using a VPN.
Similarly, if your VPN provider is compromised (through poor server security, insider threats, or government pressure), your encrypted traffic could be intercepted or logged without your knowledge.
So while the encryption itself may be rock-solid, the surrounding environment, including your own habits, can be vulnerable.
Real Examples of VPNs Getting Hacked
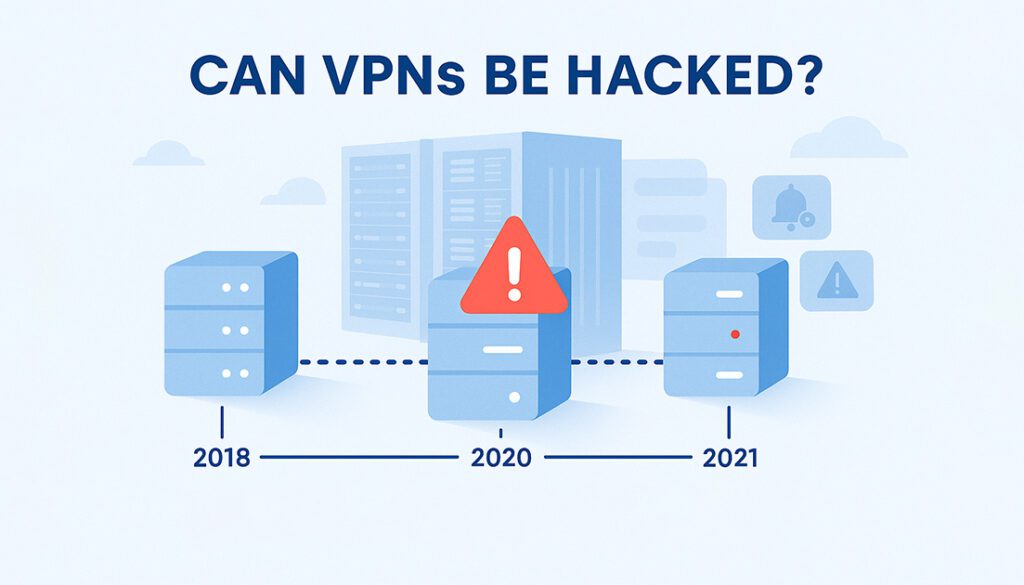
Even though VPNs are designed for privacy and security, some high-profile providers have suffered serious breaches, often due to poor server configurations or weak internal controls.
Let’s look at a few real-world cases where VPN services were compromised:
- NordVPN (2018)
In 2018, hackers accessed one of NordVPN’s servers through an insecure remote management system left by a third-party data center. Although no user data was stolen, the incident raised concerns about trust and transparency in the VPN industry. - LimeVPN (2021)
A hacker claimed to have breached LimeVPN’s database and stolen the personal data of over 69,000 users, including passwords, payment info, and logs. This incident highlighted the dangers of poorly managed VPNs. - SuperVPN, GeckoVPN, ChatVPN (2022)
A massive leak exposed the personal data of over 21 million users of these free VPNs. The leak included email addresses, passwords, and even user locations. The reason? Weak security practices and lack of encryption.
– One server was accessed through a third-party provider with a remote access vulnerability.
– No logs or user credentials were leaked, but it exposed weaknesses in infrastructure control.
– NordVPN responded by improving auditing, launching a bug bounty program, and moving to RAM-only servers.
Even top-tier VPNs aren’t immune to issues, but how they respond and improve matters just as much as the breach itself.
Common VPN Vulnerabilities Explained

While most premium VPNs use strong encryption and secure infrastructure, vulnerabilities can still arise, especially if users or providers cut corners. Below are the most common weaknesses that can lead to a compromised VPN experience:
🔓 1. DNS Leaks
A DNS leak occurs when your device sends DNS queries outside the encrypted VPN tunnel, allowing your ISP or others to see what websites you’re visiting.
🧩 2. WebRTC Leaks
WebRTC, a browser feature, can expose your real IP address even if you’re connected to a VPN, especially in browsers like Chrome or Firefox unless blocked manually.
🔐 3. Weak Encryption Protocols
Outdated protocols like PPTP or poorly implemented custom solutions can be cracked or exploited. Look for modern standards like OpenVPN, WireGuard, or IKEv2/IPSec.
🚫 4. No Kill Switch
A kill switch cuts your internet if the VPN connection drops. Without one, your traffic could leak unencrypted, even for a few seconds.
🕵️ 5. Malicious or Insecure VPN Providers
Some VPNs, especially free ones, log your data, inject ads, or even sell your info to third parties. Always vet your provider.
⚙️ 6. Misconfigurations or Unpatched Apps
Using outdated VPN apps or routers with default settings can expose you to known vulnerabilities and exploits.
– DNS or WebRTC leaks revealing your real IP
– Weak or outdated encryption protocols
– No kill switch to stop traffic leaks
– Unsafe or dishonest VPN providers
– Outdated apps or poorly configured devices
Can VPN Providers Themselves Be Trusted?

Even if a VPN uses strong encryption and has all the right features, there’s one major variable you can’t overlook: the provider itself.
When you use a VPN, you’re essentially shifting trust from your internet provider (ISP) to the VPN company. That means your browsing history, IP address, and traffic patterns could still be visible, just to a different party.
That’s why the reputation, transparency, and logging policy of the VPN provider matter more than you might think.
🚨 Real Risks from Untrustworthy VPNs:
- Some free VPNs log user data and sell it to advertisers.
- Others are owned by shady parent companies with unclear policies or government ties.
- Even some paid VPNs have vague no-log policies that don’t hold up under legal scrutiny.
– No clear no-logs policy
– Based in surveillance-heavy countries
– No third-party audits
– Owned by unknown or suspicious parent companies
– Too-good-to-be-true “free forever” offers
✅ Undergo independent security audits
✅ Operate under privacy-friendly jurisdictions
✅ Have a clear, strict no-logs policy
✅ Use RAM-only servers that wipe data on reboot
Free VPNs vs Paid VPNs: Which Are More Vulnerable?

Not all VPNs are created equal, and the biggest divide often comes down to free vs paid services.
Free VPNs might sound appealing, but they often come with serious trade-offs in privacy, security, and reliability. Since they aren’t earning money from subscriptions, many monetize by logging your data, injecting ads, or even selling your browsing history.
On the other hand, paid VPNs have the resources to invest in stronger encryption, better infrastructure, independent audits, and transparent policies. While no service is perfect, you’re far less likely to run into logging scandals, data leaks, or shady ownership.
| Feature | Free VPN | Paid VPN |
|---|---|---|
| Encryption Quality | Often weak or outdated | Military-grade protocols |
| Logging Policy | Logs data and sells info | Strict no-logs policy |
| Server Infrastructure | Cheap or rented servers | Secure, private servers |
| Transparency & Audits | None | Regular independent audits |
| Trust & Ownership | Often hidden or suspicious | Open and verified companies |
Summary:
Free VPNs often come with hidden risks, from weak encryption to shady logging practices. Paid VPNs, on the other hand, are built for security, transparency, and long-term trust. When your privacy is on the line, investing in a reliable provider is well worth it.
How to Tell If Your VPN Is Secure (Checklist)
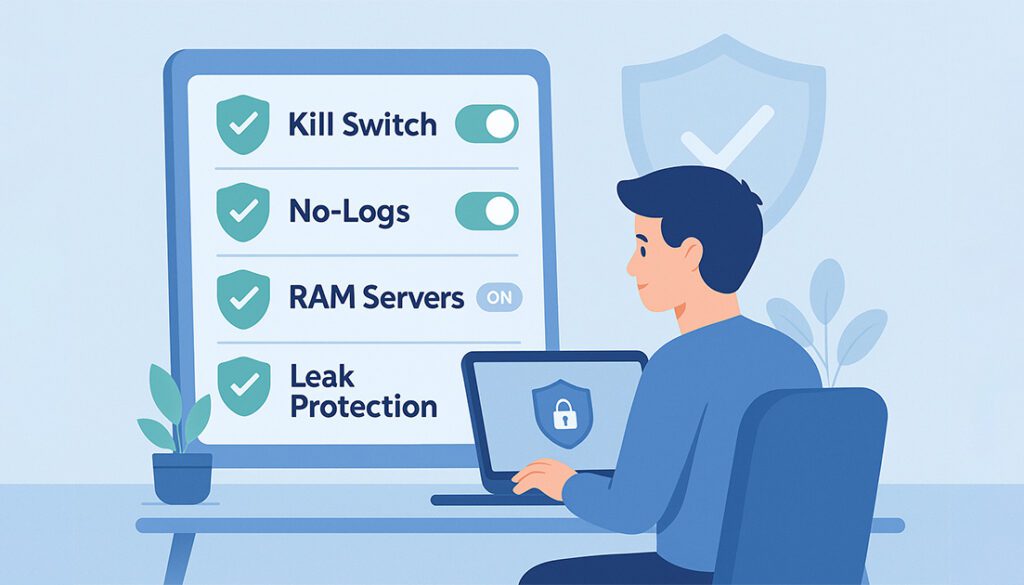
With so many VPNs out there, it can be tough to know which ones are actually secure. Here’s a simple checklist to help you evaluate whether your current VPN, or the one you’re considering, is truly safe and privacy-friendly.
Look for the following features:
- 🔐 Modern encryption protocols like WireGuard, OpenVPN, or IKEv2/IPSec
- 🚫 Strict no-logs policy, verified by third-party audits
- 🧠 RAM-only servers that wipe data on reboot
- 🛑 Kill switch to prevent IP leaks if your VPN drops
- 🌍 Leak protection for DNS, WebRTC, and IPv6
- 🔍 Independent security audits and transparent ownership
- 📍 Privacy-respecting jurisdiction (outside 5/9/14 Eyes countries)
- 📲 Actively updated apps with strong reviews and patch history
- 🧩 Multi-hop or obfuscation options for deeper anonymity
The more of these features your VPN checks off, the better your digital protection.
🔐 Secure VPN Checklist:
✅ Uses modern encryption (WireGuard, OpenVPN, IKEv2)✅ Verified no-logs policy
✅ RAM-only servers
✅ Built-in kill switch
✅ Leak protection (DNS, WebRTC, IPv6)
✅ Passed independent security audits
✅ Based in a privacy-friendly jurisdiction
✅ Frequently updated apps
✅ Offers multi-hop or obfuscation features
Tips to Stay Safe While Using a VPN

Even the most secure VPN can’t protect you if you use it carelessly. Staying safe online isn’t just about picking the right service, it’s also about using it the right way.
Here are smart habits that will help you stay protected while using a VPN:
- ✅ Always keep your VPN app and devices updated
- ✅ Enable the kill switch to block leaks during disconnects
- ✅ Run leak tests regularly to check for DNS, IP, or WebRTC leaks
- ✅ Use strong, unique passwords for your VPN and online accounts
- ✅ Avoid browser extensions or apps that could bypass your VPN tunnel
- ✅ Never trust “free” VPNs, if it’s free, you’re the product
- ✅ Enable multi-hop or obfuscation if you’re in a high-censorship country
- ✅ Combine VPN usage with private browsers or secure DNS (like DNS over HTTPS)
VPNs are powerful privacy tools, but only if used responsibly. Your habits matter just as much as the provider you choose.
Final Thoughts
A VPN is one of the best tools available to protect your privacy online, but it’s not a magic shield. While high-quality VPNs with strong security protocols are nearly impossible to hack directly, vulnerabilities can still come from weak settings, shady providers, or careless user behavior.
The good news? Most risks are avoidable. By choosing a reputable VPN and following best practices, you can significantly reduce your chances of exposure.
When used wisely, a VPN is a powerful line of defense, but like any tool, its strength depends on how you use it.
Ready to Use a Truly Secure VPN?
If you’re serious about online privacy and security, don’t gamble on shady or underpowered VPNs. Choose from our top-rated providers, all tested, audited, and built with real protection in mind.
See Our Top VPN PicksFrequently Asked Questions
Can my ISP see I’m using a VPN?
Yes, your ISP can detect that you’re connected to a VPN, typically by noticing encrypted traffic and the IP address of the VPN server. However, they cannot see the websites you visit or the content of your activity.
Has NordVPN ever been hacked?
Yes. In 2018, NordVPN confirmed that one of its servers was accessed through an insecure third-party data center. No logs or user data were compromised, and NordVPN responded by improving transparency and security standards.
Are free VPNs dangerous?
Often, yes. Many free VPNs fund themselves by logging and selling user data, showing intrusive ads, or offering weak security. Some have even been caught leaking IP addresses or storing logs despite privacy claims.
Is a VPN enough for privacy?
Not completely. A VPN is a great foundation for privacy, but it’s best used alongside tools like secure browsers, strong passwords, multi-factor authentication, and safe browsing habits.
Can a VPN protect me from malware?
No. Most VPNs do not offer direct protection from malware or viruses. You still need a good antivirus or antimalware solution to stay protected.
Can a VPN be hacked through brute force?
It’s extremely unlikely. Strong VPNs use encryption that would take thousands of years to crack using brute force. Most “hacks” occur due to app vulnerabilities or provider missteps, not from breaking the encryption itself.
Do VPNs hide your activity from Google?
Partially. A VPN can hide your IP address from Google, but if you’re signed into a Google account or using Chrome, your activity may still be tracked unless additional privacy tools are used.
Do VPNs prevent phishing attacks?
No. A VPN doesn’t block phishing emails or scam websites. Use browser-based phishing filters and common sense to avoid clicking malicious links.
What should I do if I suspect my VPN is leaking data?
Run a DNS and WebRTC leak test using tools like browserleaks.com or dnsleaktest.com. If you find a leak, switch providers or adjust your VPN settings immediately.
What is the safest VPN protocol to use?
WireGuard is currently one of the safest and fastest protocols. OpenVPN is also highly secure and trusted. Avoid older protocols like PPTP or L2TP, which are outdated and vulnerable.