With so many tools available for digital protection, it’s easy to get confused about the differences. This is especially true when comparing firewall vs proxy vs VPN, three common but very different solutions used to improve privacy, security, and control over online activity.
A firewall acts as a gatekeeper, blocking unauthorized access to or from a network. A proxy server routes traffic between a user and the internet, masking identity or enforcing content filters. A VPN, meanwhile, encrypts all traffic and routes it through a secure tunnel, protecting users from surveillance or tracking.
Still, many people wonder: What’s the real difference between them? Do you need just one or all three?
This guide breaks down the purpose, advantages, limitations, and ideal use cases for each tool so you can make informed decisions about your digital security setup.
What Is a Firewall?
A firewall is a network security system that monitors and controls incoming and outgoing traffic based on pre-defined rules. Its core purpose is to block unauthorized access while allowing legitimate data to flow freely.
🔍 How Does It Work?
Firewalls act as a barrier between your internal network and the internet. They inspect data packets and decide based on security rules whether that traffic should be allowed, denied, or flagged.
🌐 Common Use Cases
- ✅ Blocking malware, intrusions, and suspicious IPs
- ✅ Protecting home or business networks from external threats
- ✅ Enforcing access rules across ports, protocols, or IPs
- ✅ Filtering unauthorized outbound traffic from infected devices
🧱 Types of Firewalls
- Packet-Filtering Firewall: Filters traffic based on IP, port, and protocol.
- Stateful Firewall: Tracks active connections and makes dynamic filtering decisions.
- Proxy Firewall: Acts as a middle layer to inspect traffic before it reaches its destination.
- Next-Gen Firewall (NGFW): Includes features like intrusion prevention, app control, and threat intelligence.
📌 Good to Know
Firewalls typically operate at the network (Layer 3) and transport (Layer 4) levels of the OSI model, providing system-wide protection that’s essential for both individuals and organizations.
What Is a Proxy Server?
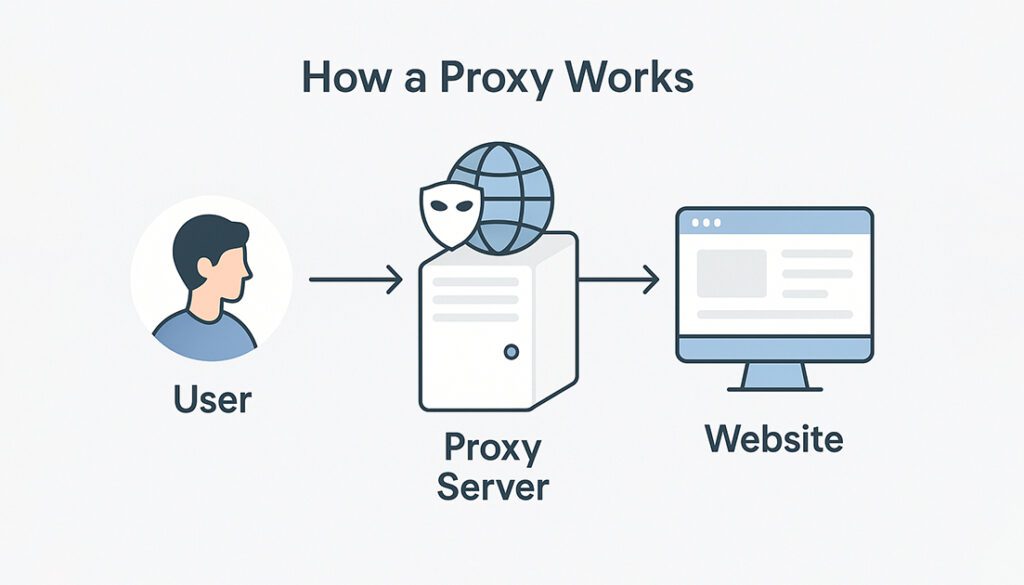
A proxy server is an intermediary that sits between your device and the internet. It processes your requests to websites or services by forwarding them on your behalf and then sending the response back to you.
This detour hides your real IP address, providing privacy and control over internet access.
🔍 How Does It Work?
When you connect to a website through a proxy:
- Your request first goes to the proxy server.
- The proxy forwards the request to the destination server.
- The website responds to the proxy, which then delivers it back to you.
The result? Your identity stays hidden, and the proxy manages traffic flow and access.
🌐 Common Use Cases
- ✅ Bypassing geo-restrictions or content blocks
- ✅ Hiding your IP address for anonymous browsing
- ✅ Web scraping and automation at scale
- ✅ Filtering content on school or business networks
🔄 Types of Proxy Servers
- Forward Proxy: Routes requests from users to the internet.
- Reverse Proxy: Routes external requests to internal servers, often used by websites and apps.
- Transparent Proxy: Operates without user knowledge, often used for caching or filtering.
- Residential or Rotating Proxy: Used for large-scale data collection or masking.
📌 Good to Know
Proxies operate at the application layer (Layer 7), making them ideal for specific apps or browsers—but they don’t encrypt traffic, which limits their security.
What Is a VPN?
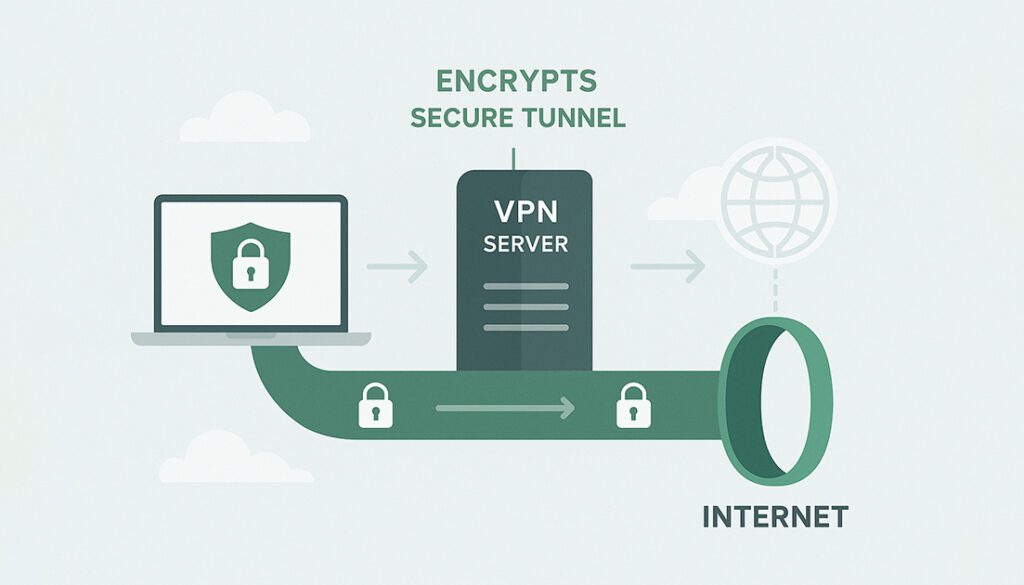
A VPN (Virtual Private Network) is a secure tunnel between your device and the internet. It encrypts your online activity and routes it through a remote server, making it appear as though you’re browsing from another location.
Unlike a proxy or firewall, a VPN protects your entire internet connection, not just specific applications or traffic types.
🔍 How Does It Work?
When you connect to a VPN:
- Your device first encrypts all data before it leaves.
- The VPN server receives and decrypts it, then sends the request to the internet.
- The response travels back through the encrypted tunnel to you.
This prevents ISPs, hackers, or governments from seeing your activity.
🌐 Common Use Cases
- ✅ Encrypting data on public Wi-Fi networks
- ✅ Bypassing geo-blocks on streaming platforms
- ✅ Preventing ISP tracking or throttling
- ✅ Maintaining privacy while working remotely
🛡️ Types of VPN Protocols
- OpenVPN: Highly secure and widely supported
- WireGuard: Modern, fast, and lightweight protocol
- IKEv2/IPSec: Great for mobile and reconnecting quickly
- L2TP/IPSec: Easy to configure but older and slower
📌 Good to Know
VPNs operate at the network level, encrypting all traffic from your device, regardless of the app. They’re ideal for privacy and data protection, but can slightly reduce speed depending on the server and protocol.
Firewall vs Proxy vs VPN: Key Differences

While firewalls, proxies, and VPNs all enhance your online security or privacy, they do so in very different ways. Here’s how they compare across critical aspects like functionality, protection level, performance, and use cases. Firewall vs Proxy vs VPN
🧱 Firewall
- Purpose: Blocks unauthorized access
- Layer: Network/Transport (Layers 3 & 4)
- Scope: System-wide traffic control
- Use Case: Enterprise, router-level protection
- Encryption: ❌ No (unless integrated)
🔄 Proxy
- Purpose: Filters and forwards requests
- Layer: Application (Layer 7)
- Scope: App-specific traffic
- Use Case: Scraping, geo-unblocking
- Encryption: ❌ No
🛡️ VPN
- Purpose: Encrypts and reroutes traffic
- Layer: Network/Transport (full-stack)
- Scope: Device-wide protection
- Use Case: Privacy, streaming, travel
- Encryption: ✅ Yes (AES-256, etc.)
Final Thoughts
- Firewalls are best for blocking threats and enforcing access rules.
- Proxies are best for anonymity, control, or task-based filtering.
- VPNs are best for full-device encryption and global privacy.
For many users and organizations, combining two or even all three creates a much stronger, more flexible defense.
When to Use a Firewall, Proxy, vs VPN
Knowing which tool to use and when, is just as important as understanding what they do. Each of these technologies fits best in specific situations. Here’s how to decide.
🧱 Use a Firewall When…
- Blocking inbound threats is your top concern
- You manage a home or office network
- You want to enforce strict access control
- You’re securing systems at the router or OS level
🔄 Use a Proxy When…
- You want to browse anonymously
- You need access to geo-restricted websites
- You’re scraping or automating web data
- You’re applying content rules on browsers/apps
🛡️ Use a VPN When…
- You’re on public Wi-Fi and need full encryption
- You want to bypass streaming blocks
- You’re working remotely or traveling
- Your ISP throttles or monitors your traffic
Can You Use All Three Together?
Yes — and in many cases, you should.
Using a firewall, proxy, and VPN together creates a layered security model, which is far more effective than relying on any single tool.
Here’s how the combination works:
- ✅ Firewall protects your entire system from unauthorized access and filters both incoming and outgoing traffic.
- ✅ Proxy server manages specific applications or requests, helping with content filtering, IP rotation, and anonymity.
- ✅ VPN adds encryption and location masking, securing all internet traffic and protecting against ISP tracking or public Wi-Fi risks.
Together, they form a strong defense strategy:
- The firewall stops unwanted intrusions.
- The proxy provides control and privacy at the app level.
- The VPN encrypts your traffic and hides your location on a system-wide level.
This combo is especially valuable for:
- Remote workers
- Business networks
- High-risk environments
- Power users managing multiple tools
However, stacking all three may introduce slight latency or require careful configuration, especially in business settings. But for those seeking maximum privacy and protection, this layered approach is hard to beat.
Cost and Value Comparison
Choosing the right tool often comes down to balancing features with cost. While firewalls, proxies, and VPNs vary in what they offer, each brings specific value depending on your goals—whether it’s privacy, control, or system-wide security.
🧱 Firewall
- Built-in OS firewalls: ✅ Free
- Business-grade solutions: 💲 $100–$1,000+
- Best for blocking threats at network level
- Ideal for routers, offices, and infrastructure
🔄 Proxy Server
- Datacenter proxies: 💲 $0.15-$2/month
- Residential/rotating: 💲 $30–$100+
- Great for scraping, access control
- Lightweight & task-specific privacy
🛡️ VPN
- Premium plans: 💲 $3–$12/month
- Free VPNs exist, but risky
- Best for privacy and full traffic encryption
- Popular for streaming, travel, and remote work
📌 Summary
If you’re looking for complete system protection, a firewall is a long-term investment. For specific privacy tasks or scraping, proxies deliver flexibility. And if your focus is encryption, privacy, and anonymity across all apps, a VPN offers excellent value especially for personal and remote use.
Pros and Cons of Each Tool
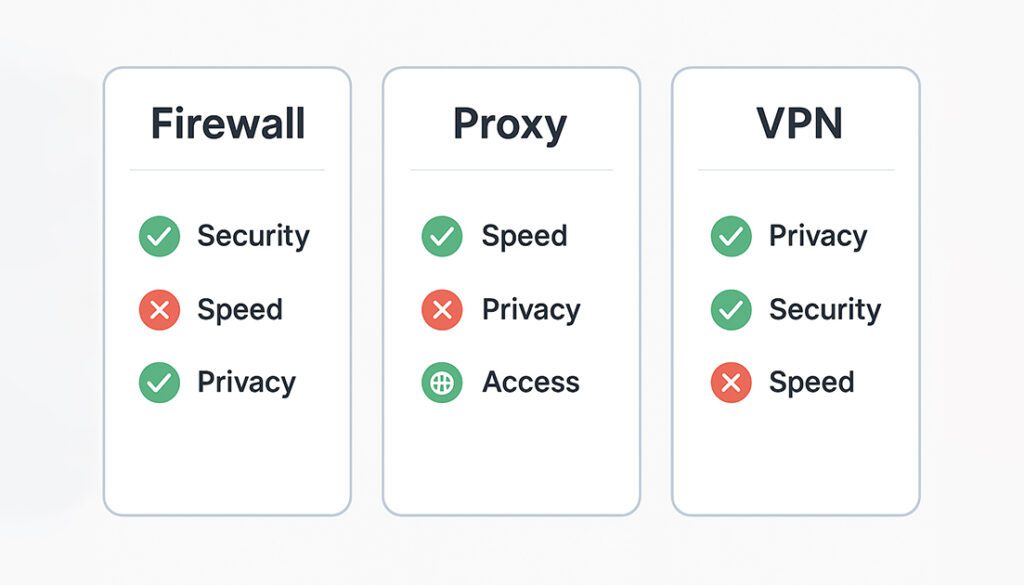
Understanding the advantages and trade-offs of each option helps you choose the right tool or combination for your privacy, security, or business needs.
🧱 Firewall
✅ Pros:
- Blocks unauthorized access
- Filters both inbound and outbound traffic
- Essential for business-grade networks
- Customizable rule sets and port control
❌ Cons:
- Can be complex to configure
- No encryption by default
- Overhead on network performance in deep packet inspection
🔄 Proxy
✅ Pros:
- Masks IP address for anonymity
- Allows content filtering and access control
- Useful for scraping, automation, and bypassing geo-blocks
- Lightweight and application-specific
❌ Cons:
- No traffic encryption
- Can be blocked by websites
- Only works on configured applications
🛡️ VPN
✅ Pros:
- Encrypts all internet traffic
- Hides IP and location from websites/ISPs
- Bypasses censorship and streaming geo-blocks
- Easy to use with system-wide coverage
❌ Cons:
- May slow down connection speed
- Quality varies between providers
- Free VPNs often log data or show ads
FAQs: Firewall vs Proxy vs VPN
Can I use a firewall, proxy, and VPN at the same time?
Yes, you can and it’s often recommended. A firewall filters harmful traffic, a proxy controls or anonymizes requests, and a VPN encrypts everything. Together, they form a layered defense.
What is the main difference between a firewall and a proxy?
A firewall blocks or allows traffic at the network level based on rules. A proxy forwards requests on behalf of the user, often hiding their IP and controlling access to content.
Does a VPN replace a firewall?
No. A VPN encrypts traffic and masks location, but it doesn’t inspect or block incoming threats. You still need a firewall for system-level protection.
Is a proxy safer than a VPN?
No. Proxies may hide your IP but they don’t encrypt traffic. A VPN provides far stronger privacy and security, especially on public networks.
Do I need a proxy if I already use a VPN?
Not necessarily. VPNs already hide your IP and encrypt traffic. However, proxies can still be useful for task-specific routing, like managing browser traffic or scraping data.
Which tool is best for streaming content?
A VPN is the best option for streaming. It can bypass geo-blocks and censorship while keeping your activity private. Many VPNs are optimized for platforms like Netflix, Hulu, and BBC iPlayer.
Do firewalls or proxies affect internet speed?
They can, but it depends on how they’re configured:
- Firewalls may slow traffic slightly if deep inspection is enabled.
- Proxies introduce minor delays during request forwarding.
- VPNs can reduce speed if you’re connected to distant servers or using slower protocols.
Conclusion: Which One Should You Use?
Firewalls, proxies, and VPNs each play a distinct role in your online security strategy.
- Use a firewall to block unwanted traffic and protect your network.
- Choose a proxy when you need content control or identity masking.
- Rely on a VPN for full encryption, privacy, and location flexibility.
For most users especially businesses and privacy-conscious individuals combining these tools offers the strongest protection. Whether you’re managing devices, streaming, or working remotely, understanding how they work together helps you stay secure in a connected world.
Looking for a Secure VPN?
Explore our top-rated VPN providers for encrypted browsing, streaming access, and full privacy online.
View Top VPN ServicesNeed Proxy or Firewall Solutions?
Discover powerful tools from leading providers:
Bright Data •
Smartproxy (Decodo) •
Cisco Firewalls •
Fortinet NGFW


